Low-hanging fruit for hackers? Abandoned accounts and accumulated rights with former employees who were never cleaned up. Permission sprawl and identity chaos are a growing risk, and with stricter audits (ISO 27001, DORA, NIS2) around the corner, a solution is imminent.
We explain what identity lifecycle management is, why it is essential right now for large organizations under high compliance pressure, and how to implement it practically. We focus on environments of 1250+ users that work with both Microsoft cloud and on-premises systems. And of course, we will discuss what's to win: control over all user and machine identities from onboarding to offboarding. In short, you know what it brings to your organization and why you need to take action right now.
What is identity lifecycle management?
Identity Lifecycle Management (ILM) is the structured management of digital identities (accounts) throughout their lifecycle within the organization. This includes all phases of an identity, from creation upon employment to change in case of job change and removal upon departure. The goal is to ensure that the right people (and systems) have the right access at the right time, and only for as long as necessary. This makes Identity Lifecycle Management (ILM) the foundation of Identity Governance.
It is important that ILM is not only about user accounts, but also about machine identities (such as service accounts, API keys, certificates). Contemporary standards such as ISO 27001:2022 require that the entire lifecycle of identities in a broad sense, i.e. of both human and non-human, is managed. This means that, for example, a server account or script user ID must be uniquely registered, authorized and ultimately cleaned just as much as an employee account. Identity lifecycle management therefore covers all entities that have access to systems in your IT environment.
Why is Identity Lifecycle Management important in 2025?
The need for ILM has never been as high as it is today. First, many large organizations struggle with permission sprawl: over time, users accumulate more and more rights than strictly necessary, known as privilege creep. Without lifecycle management, there are orphaned accounts (orphaned accounts of former employees) and redundant access rights that are not revoked. This increases the risk of abuse enormously. Out of the Verizon Data Breach Investigations Report 2025 It found that 22% of all security breaches started with the misuse of credentials and that as many as 88% of attacks on web applications involved stolen credentials. A malicious person who finds an old account or an excess of rights therefore has gold in his hands.
In addition, the compliance and audit pressure increased significantly. New legislation such as the European NIS2 Directive requires stricter measures for access and identity management sector-wide. In the financial sector, the Digital Operational Resilience Act requires (DORA) that financial institutions manage user rights in real time and perform regular access reviews to prevent privilege creep. The Dutch NCSC highlights in their basic principles among others: “Control access: Only give employees access to data and services that are needed to do their jobs.”. In other words, least privilege must be demonstrably secured. This is only possible with tight identity lifecycle management.
At the same time, the costs and consequences of identity incidents are rising. according RSAs ID IQ Report 2026 69% of organizations experienced an identity-related security incident in the past three years, a significant increase compared to the year before.
The identity lifecycle management phases (Joiner—Mover—Leaver)
Identity lifecycle management is often divided into three main phases, also known as the Joiner Mover Leaver (JML) called a model. These phases describe the lifecycle of a user identity within the organization:
- Joiner — when a new employee joins or an external employee joins. A digital identity (account) must be created for this person and provided with the correct baseline of access rights (birth rights). For example, a new account in Microsoft Entra ID (Azure AD) with default permissions for email, HR systems, and any role-based access to the feature. Ideally, this happens automatically as soon as HR registers employment, so that the new user can start (safely) immediately on day 1.
- Mover — when an existing user changes roles, departments or locations within the organization. This requires adjusting their access rights: rights that are no longer necessary must be revoked and new rights assigned to the new role. For example, an employee moves from Sales to Finance; Sales systems must be denied and access to Finance applications granted. A good JML process implements this in a timely manner, so that the user is not left with too many or too few rights. Automatic detection of such changes (e.g. via HR or AD group change) and associated workflow saves a lot of manual work here. Human error is the biggest risk.
- Leaver — when a user leaves the organization or no longer needs access. This is the crucial offboarding: all access rights must be terminated by the end date, accounts deactivated or deleted. Possibly should deleted accounts (orphaned accounts) be archived for a later audit or investigation. An effective leaver process ensures that an old account does not accidentally remain active. Think of revoking network access, VPN, SaaS accounts, and physical access cards immediately on the day of departure.
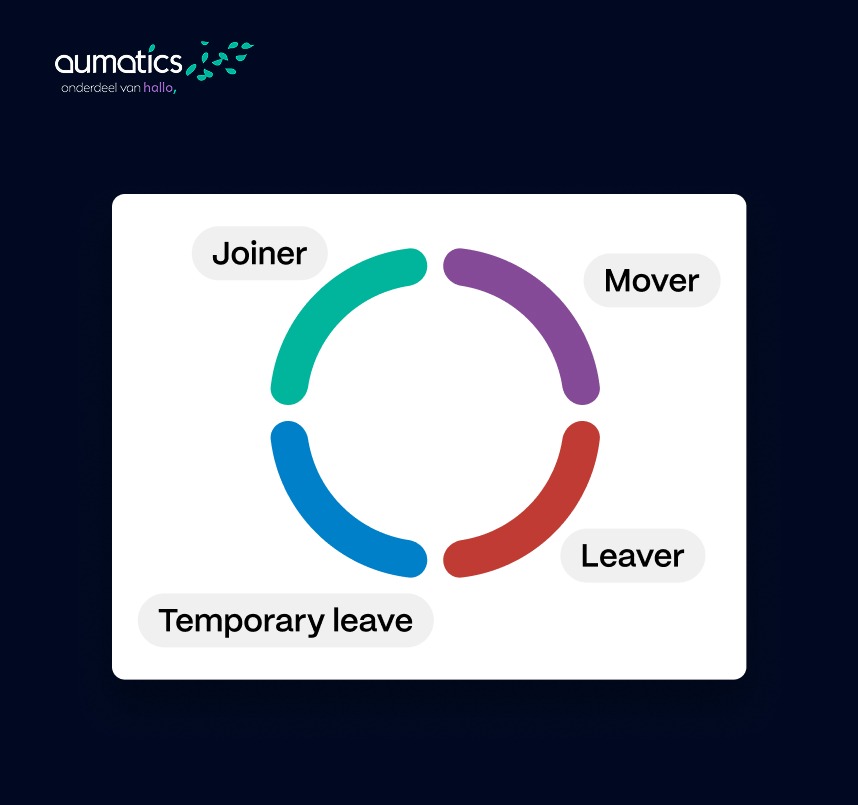
Together, these phases form the user identity lifecycle managementcycle. By having a standardized process for each joiner, mover and leaver, you maintain control. In addition, you create a logical audit trail: you can demonstrate when an account has been created, modified, and closed and based on whose authorization. By the way, this JML model not only applies to staff, but also to external partners/guests who receive temporary access.
Automated identity lifecycle management — automation as key
In small organizations, identity management can still be maintained with manual work and checklists. But in medium and large organizations, automation is essential to keep identities correct at scale. Automated identity lifecycle management means that as many steps as possible in the joiner-mover-leaver process are automated according to predefined workflows and policies. This has several advantages:
- Consistency & speed: When someone starts new or changes roles, accounts and rights are immediately created or adjusted correctly based on policy, without waiting time or human error.
- No forgotten offboardings: Automation prevents accounts from lingering after departure. As soon as HR enters a retirement, the IAM system can automatically lock all associated accounts and prepare them for removal.
- Less permission sprawl: By predefining birthright access packages and roles (RBAC/ABAC) and enforcing SOD policies, users automatically receive only minimal permissions (least privilege).
- Audit ready reports: Automated ILM records everything: who got or lost access, when, and based on what request or event. This provides a complete audit trail of each “identity mutation”.
In short, automated identity lifecycle management makes identity management more efficient, safer and controllable. However, of course, this does not work with an excel list and some half API links. You have dedicated tools and software for this.
Identity lifecycle management tools & solutions
Technology is an enabler for ILM. There are various identity lifecycle management tools and solutions on the market, ranging from built-in platform features to complete stand-alone Identity Governance & Administration (IGA) suites. Here, we discuss two categories that are often relevant to Microsoft-oriented organizations: Microsoft Entra ID Governance and fully-fledged IGA solutions (such as RSA Governance & Lifecycle). Both can serve as an identity lifecycle management solution, but there are important differences in scope and possibilities.
Microsoft Entra ID Governance
Microsoft Entra ID Governance is Microsoft's built-in solution for identity governance within the Entra (formerly Azure AD) platform. It offers policy-based and largely automated solutions to ensure that the right people have the right access to the right resources, and only for as long as necessary. Key features include Lifecycle Workflows (JML workflow automation), Access Reviews (periodic review of access rights), Entitlement Management (access packages and self-service requests), and Privileged Identity Management (PIM) for administrator accounts.
Full-fledged IGA solution (e.g. RSA Governance & Lifecycle)
For organizations that go beyond just Microsoft and want full control over all identities in hybrid environments, a full-fledged Identity Governance & Administration (IGA) solution recommended. One example is RSA Governance & Lifecycle, a leading platform that provides comprehensive governance, provisioning and compliance functionality offers both on-premises and in the cloud. Where Entra ID Governance focuses on Azure AD, RSA G&L can overlay all your systems and applications as an overarching layer. From Microsoft to other platforms, this is especially valuable when dealing with legacy provisioning, complex SOD requirements, and stringent auditing requirements.
Our RSA expert explains when and why an IgA solution is useful:
User vs machine identity lifecycle management
For a long time, identity management focused on people, but machine identity lifecycle management is just as important. Machine identities, such as application accounts, service accounts, API tokens, RPA accounts, IoT identities, and certificates, also have a lifecycle: create, use, modify, and delete.
In practice, machine accounts are often forgotten. They have no HR exit, persist after migrations and thus form orphaned credentials with high privileges. Attackers like to exploit this because machine accounts are less monitored and often have broad privileges. Identity lifecycle management must therefore include both human and non-human identities.
Getting started with Identity Lifecycle Management
Curious about how your organization can take identity lifecycle management to the next level? Aumatics stands as a security-first MSP and RSA Gold Partner waiting for you. Plan now an exploratory meeting of 30—45 minutes with our identity specialists.



