Over the past year, the number of phishing websites has increased by 27%, not to mention a few additional websites. We are talking about tens to hundreds of thousands of websites. The way of lighting is not only becoming more and more popular, but also increasingly difficult to recognize. The e-mails look more and more like, and in some cases are almost identical to e-mails that you would normally click on without thinking.
This is exactly the trap that people keep falling into. To avoid this, you should always ask yourself a few questions before you decide to click on anything. For example, you should ask yourself whether you know the sender, whether the sender's email address is legitimate and whether you expected the email. An example; Don't expect to get a large amount of money deposited into your account? If that is not the case, then the chance is also quite small that you will receive an email with congratulations of a sum of one and a half million money to be claimed from a Zimbabwean prince.
Below we show a number of examples of phishing emails that we also cover in the white paper. A note beforehand; read your own name in the places where {name} and {surname} are written. That way you would also receive the email in your inbox. Be honest with yourself whether you would click on the link!
Example 1
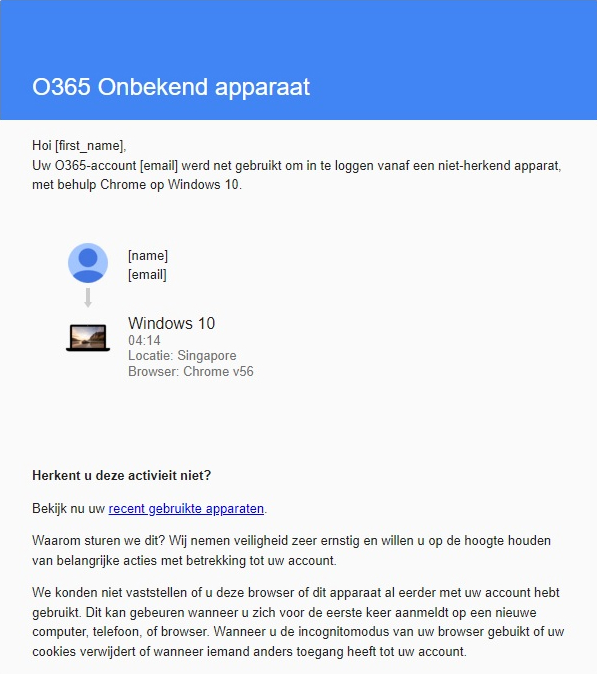

Example 2
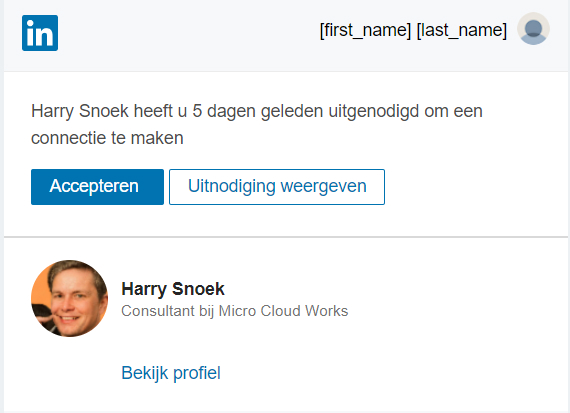



Example 3
And? How well do you recognize the phishing emails? We cover the subject of phishing emails in depth in our white paper, in which we conclude with a number of recommendations. Do you want to know how you can best arm yourself against phishing? Download our white paper.






























